Understanding the OSI Model: Layer 7 – The Application Layer
Sirr Gardener
12/15/20244 min read

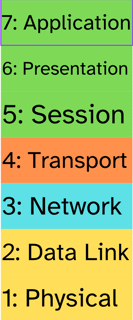
The OSI (Open Systems Interconnection) model is a foundational framework for understanding how data travels across networks. At the very top of this model lies Layer 7: The Application Layer, which directly interacts with end-users and their applications. In this blog post, we’ll delve into the functionality, significance, and practical applications of the Application Layer, illustrating how it serves as the gateway between human interactions and the underlying network processes.
What Is the Application Layer?
The Application Layer is the seventh and final layer of the OSI model. Unlike the layers below it, which focus on the mechanics of data transfer, the Application Layer is all about enabling communication between users and applications.
This layer provides the tools and interfaces that allow software applications to interact with the network. It is where end-user services reside, making it the most visible and user-oriented layer of the OSI model.
Functions of the Application Layer
The Application Layer performs several critical tasks to facilitate meaningful communication over a network:
Network Access for Applications:
Provides an interface between the application and the network, enabling software to send and receive data.
Example: A web browser (application) uses HTTP to retrieve web pages from a server.
Data Presentation to Users:
Ensures that data received from lower layers is presented in a format that applications and users can understand.
Resource Sharing and Remote Access:
Supports remote file access, printer sharing, and other resource-sharing functionalities.
Service Advertisement:
Allows devices or services to announce their availability on the network.
Example: A network printer advertising its presence to nearby computers.
Authentication and Authorization:
Ensures that only authorized users or devices can access specific resources or services.
Example: Logging into an email account securely.
Error Detection and Handling:
Alerts the user or application if issues arise, such as unavailable servers or incorrect data formatting.
Real-World Use Cases of the Application Layer
The Application Layer is integral to many everyday activities, including:
Web Browsing:
Protocols like HTTP and HTTPS enable users to access websites. The browser (application) uses these protocols to request and display web pages.
Email Communication:
Protocols such as SMTP, POP3, and IMAP handle sending and retrieving emails.
File Transfers:
FTP (File Transfer Protocol) allows users to upload or download files between devices.
Streaming Services:
Applications like Netflix and Spotify rely on Application Layer protocols to deliver media content.
Remote Desktop Access:
Protocols like RDP (Remote Desktop Protocol) enable users to control remote systems.
Online Gaming:
Game clients use Application Layer protocols to communicate with game servers, enabling multiplayer gameplay.
VoIP and Messaging Services:
Protocols like SIP (Session Initiation Protocol) and XMPP (Extensible Messaging and Presence Protocol) support voice and messaging applications.
Key Protocols at the Application Layer
The Application Layer encompasses a wide range of protocols, each designed for specific tasks:
HTTP/HTTPS (Hypertext Transfer Protocol/Secure):
Used for web browsing and data exchange on the internet.
HTTPS adds encryption for secure communication.
FTP (File Transfer Protocol):
Transfers files between systems over a network.
SMTP/POP3/IMAP (Simple Mail Transfer Protocol/Post Office Protocol/Internet Message Access Protocol):
Handle email transmission, retrieval, and storage.
DNS (Domain Name System):
Translates domain names into IP addresses.
Telnet and SSH (Secure Shell):
Provide remote access to systems, with SSH offering encryption for security.
SNMP (Simple Network Management Protocol):
Enables monitoring and management of network devices.
How the Application Layer Works
To understand the Application Layer in action, let’s walk through a typical web browsing scenario:
User Request:
A user types a URL into their browser (application).
The browser interacts with the Application Layer to initiate an HTTP/HTTPS request.
Protocol Interaction:
The HTTP protocol formats the request and sends it to the web server.
Server Response:
The web server processes the request and sends back the requested data (e.g., an HTML page).
Data Presentation:
The browser receives the response, interprets the HTML, and displays the webpage to the user.
At each step, the Application Layer ensures that communication is properly formatted and understood by both the user and the network.
Importance of the Application Layer
The Application Layer is crucial for enabling communication between users and networks. Its importance lies in the following areas:
User Interaction:
This layer is the primary interface between users and networked services, making it indispensable for user experience.
Diverse Functionality:
Supports a broad range of applications, from web browsing to file sharing and beyond.
Standardization:
Provides standardized protocols that enable compatibility across different devices, operating systems, and applications.
Security and Reliability:
Incorporates authentication, encryption, and error handling to ensure secure and reliable communication.
Challenges and Considerations
While the Application Layer provides significant benefits, it also presents challenges:
Security Risks:
Vulnerabilities in Application Layer protocols, such as HTTP or FTP, can be exploited by attackers.
Performance Overheads:
Complex protocols or resource-heavy applications can slow down network communication.
Compatibility Issues:
Variations in protocol implementations across devices or systems can cause interoperability problems.
Scalability:
Supporting a growing number of users and services requires efficient protocol design and robust infrastructure.
Conclusion
The Application Layer is the crown jewel of the OSI model, directly enabling the services and applications we rely on daily. From browsing the web to streaming media, this layer bridges the gap between human interaction and the intricate processes of network communication.
By understanding the Application Layer’s functions, protocols, and challenges, networking professionals can design and maintain systems that are secure, reliable, and user-friendly. Mastering this layer is a key step in demystifying the complexities of modern networks and ensuring seamless digital experiences for users worldwide.
