Breaking Down SSAE 18 SOC 2 Reports: A Deep Dive into Trust, Security, and Assurance
SSAE 18
Sirr Gardener
4/13/20253 min read
In a world where organizations rely heavily on third-party vendors for data storage, cloud infrastructure, and software delivery, it’s no longer enough to just say your systems are secure—you have to prove it. That’s exactly what the SOC 2 report does.
SOC 2 reports, developed under the SSAE 18 framework by the AICPA, are designed to evaluate the effectiveness of internal controls relevant to data security, availability, processing integrity, confidentiality, and privacy.
In this post, we’ll take a deep dive into SOC 2 reports: what they are, how they work, and why they matter to service organizations and their clients.
What is a SOC 2 Report?
SOC 2 (System and Organization Controls 2) is a type of audit report designed to assess a service organization's controls relevant to the Trust Services Criteria (TSC), rather than financial reporting.
SOC 2 is not a regulatory requirement, but it has become an industry-standard security and compliance benchmark for technology, cloud, and SaaS companies.
SOC 2 vs. SOC 1: What's the Difference?
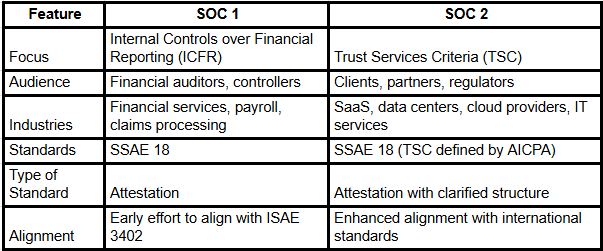
TL;DR: SOC 1 = finance,
SOC 2 = security and operational integrity.
Trust Services Criteria (TSC)
SOC 2 engagements are structured around five key principles, known as the Trust Services Criteria:
Security (required): Protection of systems from unauthorized access.
Availability: Systems are available for operation and use as agreed.
Processing Integrity: System processing is complete, valid, accurate, timely, and authorized.
Confidentiality: Information designated as confidential is protected.
Privacy: Personal information is collected, used, and retained in compliance with privacy laws.
Every SOC 2 report must include Security; the others are optional and based on services offered.
SOC 2 Type I vs. Type II
Similar to SOC 1, SOC 2 comes in two types:
✅ SOC 2 Type I
Examines the design of controls at a specific point in time.
Answers: “Are the controls suitably designed as of this date?”
✅ SOC 2 Type II
Evaluates the design and operating effectiveness over a period (usually 6–12 months).
Answers: “Are the controls suitably designed and functioning over time?”
Clients and vendors usually prefer Type II reports for greater assurance.
Anatomy of a SOC 2 Report
SOC 2 reports typically include:
1. Auditor’s Opinion
Independent CPA firm’s conclusion on the effectiveness of the controls.
2. Management’s Assertion
Statement by the service organization’s management affirming the system description and control environment.
3. System Description
Overview of the organization’s services, infrastructure, software, people, procedures, and data.
4. Criteria, Controls, and Tests
Lists of controls mapped to each relevant Trust Services Criterion.
Type II reports also include test procedures and results.
5. Complementary User Entity Controls (CUECs)
Controls that clients (user entities) must implement for the system controls to work effectively.
SOC 2 Audit Process
The typical SOC 2 engagement follows these steps:
🔍 1. Scoping
Define which services and Trust Services Criteria are in scope.
🧪 2. Readiness Assessment (optional but recommended)
Identify gaps in existing controls before the formal audit.
📝 3. Documentation
Prepare policies, procedures, control narratives, and evidence of implementation.
👨💼 4. Audit Fieldwork
The auditor reviews evidence, interviews staff, and tests controls (for Type II).
✅ 5. Report Issuance
Final SOC 2 report is issued and valid for 12 months from the end of the audit period.
Why SOC 2 Matters
In a market driven by trust and data assurance, SOC 2 is often a deal-breaker or deal-maker. It provides organizations with an independently verified way to demonstrate they’re protecting their customers’ data.
🚀 Benefits for Service Organizations:
Build trust with prospects and customers
Meet procurement and compliance requirements
Stand out in competitive B2B markets
Improve internal security posture
✅ Benefits for Clients:
Confidence in data protection and service reliability
Reduced risk of compliance failures or data breaches
Easier vendor risk management
SOC 2 and Other Frameworks
SOC 2 aligns well with other standards but isn’t a direct replacement. Here's how it compares:
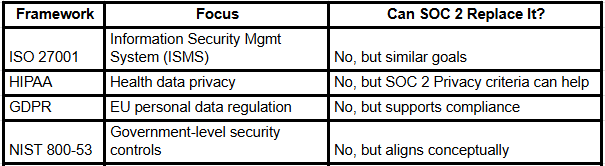
Tips for a Successful SOC 2 Audit
Start with a readiness assessment to identify control gaps.
Define clear roles and responsibilities for audit preparation.
Document everything—especially policies, access logs, and incident responses.
Automate evidence collection where possible (e.g., security logs, backups).
Ensure ongoing compliance, not just during the audit window.
Final Thoughts
SOC 2 reports are more than just audit deliverables—they’re strategic assets that validate your commitment to secure, reliable, and compliant operations. For technology and service providers, a clean SOC 2 Type II report can open doors to enterprise clients, streamline vendor reviews, and enhance operational maturity.
Whether you're just starting the SOC 2 journey or preparing for your next annual engagement, understanding the process and aligning with the Trust Services Criteria is essential for long-term success.
Further Reading
AICPA Trust Services Criteria
SOC 2 vs. ISO 27001: What’s the Difference?
Guide to Preparing for a SOC 2 Type II Audit
